#file name: updated user policy
Explore tagged Tumblr posts
Text

A theoretical scene for chapter 23 of A Dark Among the Lights by LuckyLectio on AO3.
Fun fact: this was supposed to be a silly doodle since I was tired. However, being sleepy, I went on autopilot and was halfway through coloring the darn thing when I realized what was happening.
#file name: updated user policy#hylia's design is also picked up from luckylectio--though the colors were yoinked from goddess plumes and the goddess sword from loz ss#her hair gave me so much trouble. i could not decide between purple and blonde#she kinda has lavender vibes now#hey look! i finally drew fi under normal circumstances#but circling back to lectio's design--it's so fun and flowy and decorative#i had fun drawing her#gonna go lay down now. this week has been a lot#adatl#loz hylia#loz fi#my art
152 notes
·
View notes
Text
Alright. I'm making this post because I was unpleasantly surprised to find Microsoft had forcibly downloaded an """"ai assistant"""" onto my computer (called Copilot), and because finding a site that actually told me how to kill it for good -- in clear, truly step-by-step terms -- was way harder than it needed to be.
Preface: this is only relevant if you're running Windows 11.
Here is your target:

If you see this logo on your taskbar -- or... have Edge installed on Windows 11 -- you've got Copilot. You can't delete it on its own, Microsoft has integrated it into the OS as best they can. The most you can do is disable it (instructions for which are at the very end of this post).
So... to REALLY get rid of it you need to uninstall Microsoft Edge, because it's a part of/reliant on Edge. A lot of bells and whistles of Windows are also reliant on Edge, like widgets, but I never use those. I use my PC almost exclusively for gaming, and I don't want this slimy "ai" shit on my computer. I use Firefox anyway. Edge can go die as far as I'm concerned.
Here's the actual steps, copy-pasted from a website that took me way too long to find. It also really makes my browser chug for some reason, which is why I'm copy-pasting the whole thing. If you still want to look at the site itself, put it in reader view as fast as you can (link to site).
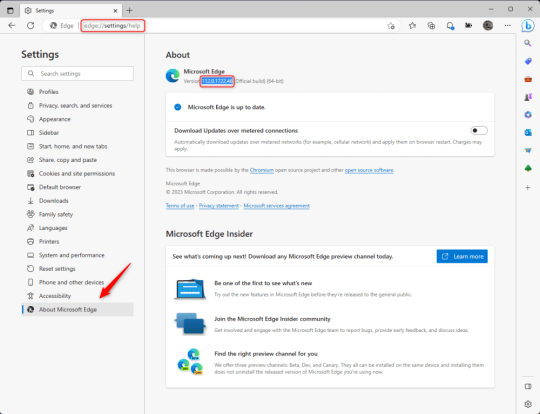
1.) Open Microsoft Edge, type "edge://settings/help" in the address bar, and then press Enter.
2.) Click "About Microsoft Edge" at the bottom of the left-hand pane. Copy the version number at the top of the screen, under Microsoft Edge.
3.) Press Windows Key + S to open Windows Search.
4.) Type "Command Prompt", right-click the result, and then select "Run as Administrator".
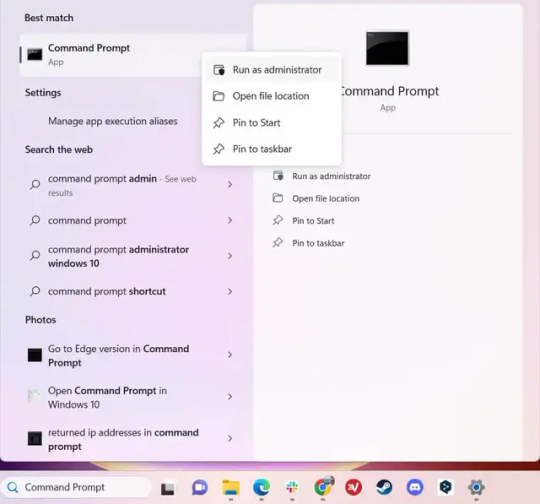
5.) The User Account Control (UAC) prompt will appear. Click "Yes".
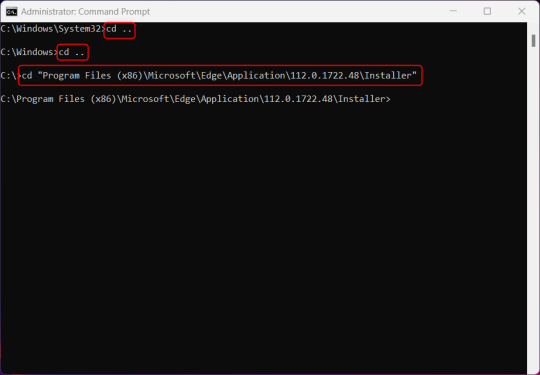
6.) Navigate to Edge’s “Installer” directory by using the cd command. Depending on which directory your Command Prompt opens in by default, you may need to use the "cd .." command to go back a level or two.
Once ready, run this command:
cd “Program Files (x86)\Microsoft\Edge\Application\Version Number\Installer”
Replace "Version Number" with your actual version number copied earlier.
7.) Next, run this command to uninstall Microsoft Edge:
setup –uninstall –force-uninstall –system-level
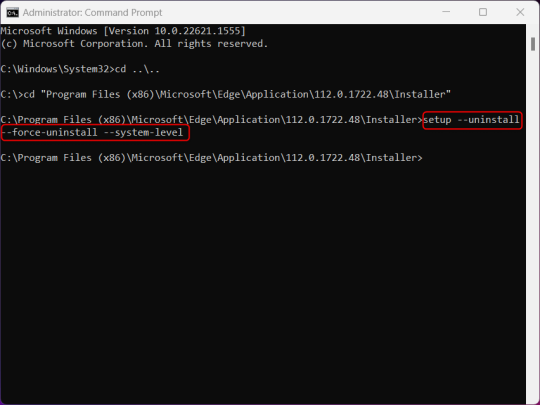
((It will look like nothing happened! Don't worry!))
8.) Restart your PC for the changes to take place.
((HOWEVER, Windows will try to reinstall it the next time your PC updates (or whenever it feels like it lol) so there's a second half to this))
1.) Press Windows Key + R to open Run.
2.) Type "regedit" in the text box and click OK to open the Registry Editor.
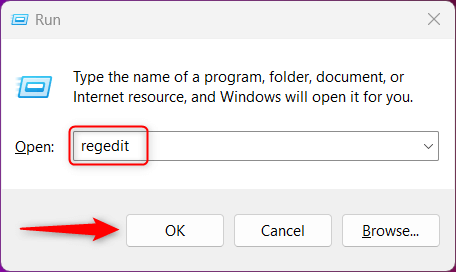
3.) The User Account Control (UAC) prompt will appear. Click "Yes".
4.) In the Registry Editor, navigate to HKEY_LOCAL_MACHINES\SOFTWARE\Microsoft.
5.) Right-click the "Microsoft" folder, hover your cursor over "New", and then select "Key".
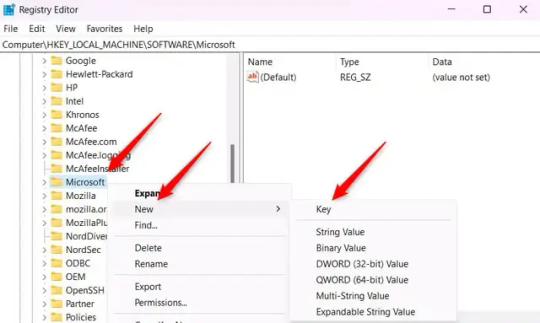
6.) Rename the new Key to "EdgeUpdate".
7.) Right-click EdgeUpdate, hover your cursor over "New", and then select "DWORD (32-bit) Value".
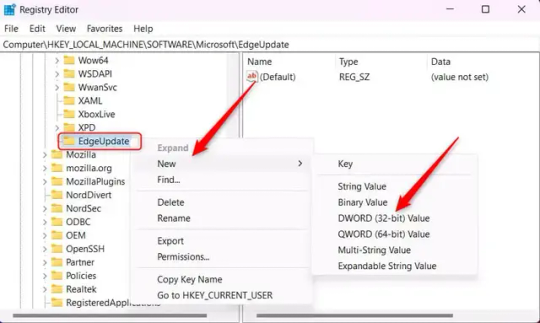
8.) Right-click the new value, which is currently named "New Value #1".
9.) Select "Rename" from the context menu.
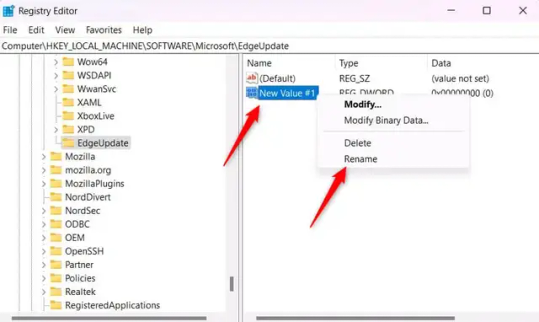
10.) Rename the value to "DoNotUpdateToEdgeWithChromium".
11.) Right-click the newly-named DoNotUpdateToEdgeWithChromium value and select "Modify" from the context menu.
12.) The Edit DWORD (32-bit) Value window will appear. Change the Value data to "1" and then click OK.
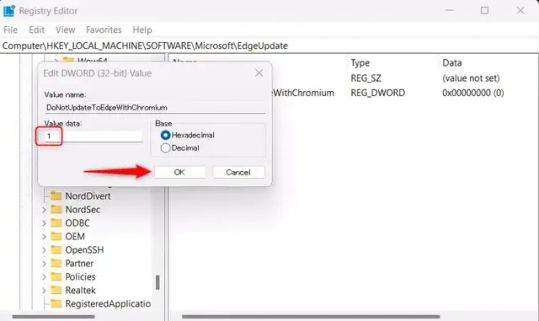
((You are now free. If you ever run into a really serious, unavoidable issue with your OS that's clearly a result of Edge being gone, you can redownload it like a regular app. But you should be fine.))
((And, if for some reason you want still want Edge around but just want the copilot thing gone, here's what you do:
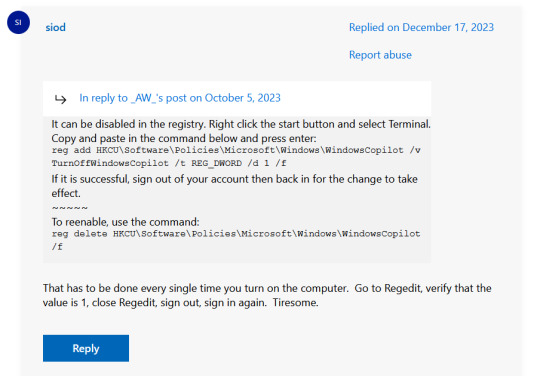
The command, for ease of copy-pasting: reg add HKCU\Software\Policies\Microsoft\Windows\WindowsCopilot /v TurnOffWindowsCopilot /t REG_DWORD /d 1 /f
You can't actually truly delete Copilot (without deleting Edge), only disable it. And as the reply says, you do have to do this every time you turn the computer on. I haven't tested that myself, but I believe it. I assume/hope that excludes just waking the computer up after it goes to sleep, but I don't know for sure.))
120 notes
·
View notes
Text
It's a day like any other, or so you think. There's nothing remarkable about it, the boss has an after-hours server update scheduled, but for you there's nothing really remarkable about it since you're not on the team for that project. It seems, in fact, like an ordinary day. IT really runs the company. The C-suite? They think they run it, but they're so clueless about the architecture their power is built on, you have more job security than a tenured professor at an ivy league school. You get all manner of calls from all across the company because people without a lick of computing sense get hired and fired on such a regular basis you don't even remember the names of the people who started on the same day as you.
Except for IT, nearly everyone in that department is secure in their job because to ordinary people, you're wizards. And everyone knows you don't mess with the wizard. They can make sure your email gets to you that contains the estimate from the vendor that will make or break your career with the company...or they can take a long lunch because you pissed them off. Yes, everyone knows not to mess with IT.
You hear the grumblings, of course. People upset they can't check their personal email on their work computer, people pissed they can't look up their fantasy football numbers if they're on the company's wifi, but they know they're powerless before you. And you like it that way. The artists you went to school with are all struggling at their coffee shop or fast food jobs, the business majors are doing the crabs-in-a-bucket thing they like making analogies for, and the women who swore they'd be the change they wanted to see in the world by getting into IT all found other jobs that weren't so full of men who questioned their worth.
Your life is pretty good, your job is secure, but your peace of mind is done...you just don't know it yet. Because something happened somewhere else in the company that will shatter that peace you think you've made for yourself.
And it starts with an on-boarding ticket.
You don't think much of it, it's pretty standard stuff for a new hire. You set up their account up, filling in all the right fields and checking all the right boxes and call it done.
Then the next day you get a support ticket. You don't connect it to the on-boarding ticket at first, but it's a request for updating the email and signature information for an account that was apparently made in error. Curious, you check it out and discover that the name the user wants to use isn't their actual name, it's some off the wall hippy-dippy looking name with a weird spelling. Same last name though, so you're pretty sure it is, indeed, the person the email account is registered to. Well, company policy is to use the person's legal name on all correspondence, so you copy the boilerplate from the company manual and close the ticket.
An hour later, the ticket is reopened with HR being CC'd on the correspondence. Shit, the user is a transwoman. Company policy has an exception that allows people to use their preferred name and pronouns in company correspondence as long as Accounting, Payroll, and Legal have their legal names on file. You make the correction and close the ticket.
It's quiet for a bit after that. In fact, it's too quiet. You don't really notice it at first, after all there's always something to do, and when you run out of those things you can use your Admin rights to run one of those games you don't allow anywhere else on the network or access one of those sites that aren't permitted by the company firewall because it's good to be the king, amirite? But suddenly you start realizing you're feeling a bit like the Maytag Man. Users aren't sending in tickets to get their passwords reset or make their mouse work. In fact, the number of times the C-suite has told someone on the team to come up to their office has dropped, too.
Then the tide starts to turn...and you're getting asks both in tickets and during meetings from your boss, "We have a new procedure we're doing, it's going to eliminate the use of email for a certain process and we need you to set up xyz so this team has proper access." What's xyz? Damned if you know, you've never heard of it. You look it up and it turns out to be an older piece of collaboration software based on some open source project you've never bothered learning, but it's still being supported by the vendor (some guy who retired 10 years ago but keeps the software running for funzies) and the community. Whatever, your job is to install the software, make it work, and then handhold the PEBKACs until the crying and whining stops.
Only...the crying and whining doesn't even start. In fact, the only real problem is because...someone on your own team fucked up the roll-out and your boss got chewed and the guy who fucked it up is on notice. "Assuming IT knows the business better than the people who run it," they said. Can you imagine? The villagers questioning the wizards?
The trend continues. IT getting fewer calls, your job becoming less and less easy and more stressful as things that used to fly under the radar are being scrutinized. Forget playing that MMO on your lunch break, you're stuck playing some F2P game on your phone because someone pointed out that the firewall ports for the game were wide open and were only really used by that one game.
Nobody's been able to find the snitch, but it has to be someone in IT, right?
More and more the job becomes less and less fun as you feel the power shift from IT, who used to be the unquestioning masters of the software the business could run, back to the leadership teams of the various departments, and all under the watchful eye of the people in the highest positions of power in the office.
Then one day, one fateful day so disconnected from the day that everything changed you don't, at first, recognize the moment for what it is, you get a call from an office on the second floor. It's one of the "hotel" suites for employees who work from home but need to be in the office occasionally. It seems that the employee is trying to use a docking station that has a busted Ethernet port. They can't connect to the network so can't send a ticket the usual way.
Of course, it's not actually the Ethernet port, it never is. So you have them go through all the steps to get their computer conne...it's not connecting. Okay, so you have them unplug and plug it all ba...they said they just did all that and it's still not working. Including the Ethernet cable? Yes, including the Ethernet cable. You realize you're going to have to go up with a new docking station just in case, in the wild possibility, this user is right. You'll be right up, sir. They remind you of their pronouns. Oh, right, the user is a transwoman. You'll be right up, ma'am.
You get there and realize that the voice doesn't do them justice. They're professionally feminine and femininely professional. They're wearing nice clothes that you couldn't normally be assed to notice, but this is your first transwoman you've encountered in the wild, and you expected a walking stereotype, not someone that looks like they could have stepped off a cover of some business quarterly magazine. Her makeup is on point, her workstation is a touch messy and has a couple of nods to portable personalization. There's an anime figurine right next to her cell phone, which is in a pink, sparkly case. The moment you enter, she locks her computer, showing an incredibly good eye for InfoSec that you don't normally see in users, and you notice the lock screen on her computer has a background showing Tux the Penguin.
Later, you realize that this was the red flag that should have been your clue that your comfortable career with the company was long gone.
You do the usual check to confirm that everything she said she did had been done, test the docking station and confirm that, yes, the Ethernet port is, indeed bad. You set about replacing it and strike up conversation. When did she start with the company? Oh, that many months ago? What does she do? Oh, she specializes in finding solutions to processes that cost the company too much money. How long has she been doing that? Oh, a few years now, it was a bit of a career change but she's honestly enjoying it, finding a sense of purpose she never expected after her late in life change of path. What did she do before?
And that's when she says something that makes the blood in your veins run cold and the hairs to stand up on the back of your neck.
She used to be in IT, before her transition. She was pretty good at it, specializing in InfoSec and malware wrangling, but when she came out and transitioned suddenly she wasn't welcome in the boy's club (her exact words) anymore and needed to find something new for her own well-being and mental health.
She says this with a tiny, ever so slight smile on her face, but the look in her eye is predatory. She knows what kind of terror she struck in you in that moment. She knows because she's been there before.
She knows that the worst enemy of any IT department...is someone who used to work in IT.
You do your best to keep the chatter friendly (don't show your fear) and remove the faulty docking station and scurry back down to your cooler-than-the-rest-of-the-building office where you let the fight or flight response work its way through your system. You wonder how you're going to tell the rest of the team.
You all may be wizards, but a goddamn dragon has claimed her territory.
126K notes
·
View notes
Text
Why Healthcare Websites Need HIPAA-Compliant Web Development
In the healthcare industry, trust is everything—and that trust starts with how patient information is handled online. As more clinics, hospitals, and telehealth platforms digitize their services, protecting sensitive health data isn’t just good practice—it’s the law. That’s where HIPAA-compliant web development comes in.
A skilled Web Development Company ensures that healthcare websites meet the rigorous standards of the Health Insurance Portability and Accountability Act (HIPAA), helping organizations avoid legal risks while maintaining the privacy and security of patient information.
So what does HIPAA compliance mean in web development—and why does it matter so much?
What Is HIPAA and Why Does It Apply to Websites?
HIPAA is a U.S. federal law that regulates how protected health information (PHI) is collected, stored, accessed, and transmitted. PHI includes anything from a patient’s name and address to medical history, insurance information, or even appointment dates—any data that connects health records with personal identity.
If your website includes:
Contact or appointment forms
Patient portals
Online chat or messaging with medical professionals
Telehealth video integrations
Billing/payment systems tied to patient data
…then it must be HIPAA-compliant.
The Cost of Non-Compliance
Ignoring HIPAA compliance isn’t just a technical oversight—it’s a legal liability. Healthcare organizations that fail to meet HIPAA standards face:
Fines ranging from $100 to $50,000 per violation
Reputational damage due to data breaches
Lawsuits and patient distrust
That’s why web development for healthcare must go beyond basic functionality and focus on secure, compliant digital infrastructure.
Key HIPAA Compliance Requirements for Web Development
When building a HIPAA-compliant website, development teams focus on both technical safeguards and process-oriented policies. Here are the most important components:
1. End-to-End Data Encryption
All PHI transmitted through the website—whether in contact forms, file uploads, or appointment scheduling—must be encrypted both in transit (via HTTPS/SSL) and at rest (within databases or file storage systems).
This ensures that even if the data is intercepted, it remains unreadable to unauthorized parties.
2. Secure Authentication and Access Control
Only authorized users (e.g., patients, healthcare staff, administrators) should be able to access sensitive data. Developers implement:
Strong password policies
Multi-factor authentication (MFA)
Role-based access control (RBAC)
Session timeout and activity logs
This prevents unauthorized access and maintains a clear audit trail of who accessed what and when.
3. Business Associate Agreements (BAAs)
If your website uses third-party tools like cloud storage, analytics, or telehealth integrations that touch PHI, those vendors must also be HIPAA-compliant. A Business Associate Agreement (BAA) is required to legally define each party’s responsibility for protecting patient data.
A reputable development agency ensures that any integrations (e.g., AWS, Google Cloud, Twilio, Stripe) are covered by signed BAAs before launch.
4. Secure Hosting Infrastructure
HIPAA-compliant websites require secure, dedicated hosting environments. That includes:
Firewalls and intrusion detection systems
Isolated servers or private cloud environments
Routine vulnerability scans and updates
Encrypted data backups
Shared hosting or low-cost providers typically don't meet HIPAA standards, making hosting configuration a critical decision point.
5. Secure Forms and File Uploads
Contact forms, patient intake forms, and file upload tools must be:
Served over HTTPS
Encrypted at submission and storage
Protected by CAPTCHA to avoid spam bots
Sanitized to prevent code injection attacks
Even simple forms become a compliance risk if not implemented securely.
6. Audit Logging and Monitoring
Websites that handle PHI must include detailed logging and monitoring to detect suspicious activity and trace any breaches or misuse.
Logs should track:
Login attempts
Data access events
File downloads or changes
System errors or unauthorized access attempts
These logs must be secured and retained as part of ongoing compliance.
7. User Consent and Privacy Policies
Healthcare websites must include clear privacy policies that explain how data is collected, stored, and used. Consent checkboxes or opt-ins should be added to forms and data collection areas, aligning with both HIPAA and broader privacy best practices.
Conclusion
In healthcare, digital convenience must never come at the cost of patient privacy. Whether you’re launching a telehealth platform, upgrading a clinic website, or adding appointment scheduling tools, HIPAA-compliant web development is essential to building trust and staying legally protected.
Partnering with a Web Development Company that understands healthcare regulations ensures your site does more than just look professional—it meets the highest standards of privacy, security, and compliance. In an industry where data protection is mission-critical, that’s the peace of mind your team—and your patients—deserve.
0 notes
Text
IEC Registration: A Complete Guide to Import Export Code in India
Introduction
If you're planning to start an import or export business in India, the first and foremost requirement is obtaining the IEC – Import Export Code. Issued by the Director General of Foreign Trade (DGFT), the IEC is a 10-digit unique code that is mandatory for anyone involved in the international trade of goods or services from India.
This article will guide you through the meaning, importance, eligibility, required documents, and step-by-step process of getting your IEC registration done online.
What is IEC (Import Export Code)?
The Import Export Code (IEC) is a unique 10-digit number issued by the Directorate General of Foreign Trade (DGFT) under the Ministry of Commerce and Industry, Government of India. It is required by businesses or individuals who wish to import or export goods and services from India.
Without an IEC, businesses cannot legally engage in international trade.
Who Needs IEC Registration?
IEC is mandatory for:
Importers – to clear shipments through customs
Exporters – to send shipments abroad
Freelancers and service exporters – if foreign remittances are involved
E-commerce sellers, who export products or services outside India
Note: IEC is not required for personal use imports/exports, and is not mandatory for service exports unless benefits are claimed under the Foreign Trade Policy.
Benefits of IEC Registration
International Market Access – Opens doors to global business expansion.
Government Benefits – Avail export promotion schemes like MEIS, SEIS, etc.
Easy Compliance – Once obtained, the IEC has lifetime validity, with minimal compliance.
No Return Filing – No need to file monthly or annual returns for IEC.
Quick Processing – The Entire application can be completed online within 1-2 days.
Documents Required for IEC Registration
You’ll need the following documents:
PAN Card – of the business or individual
Identity Proof – Aadhaar card / Passport / Voter ID
Address Proof – Electricity bill / Rent agreement / Sale deed
Bank Certificate or Cancelled Cheque
Digital Photograph – Passport-size
Business Registration Certificate – (For companies, LLPs, etc.)
How to Apply for IEC Registration (Online Process)
Follow these simple steps:
Step 1: Visit the DGFT Website
Go to the official DGFT portal – https://dgft.gov.in
Step 2: Register on the DGFT Portal
Create your user profile with a valid email and mobile number.
Step 3: Fill IEC Application Form (ANF 2A)
Provide business details, PAN, bank info, and upload required documents.
Step 4: Pay Application Fee
Pay the government fee of Rs. 500 via net banking or card.
Step 5: Submit and Track
Submit the form. You will receive the IEC certificate on your registered email, usually within 1-2 working days.
Validity & Renewal
The IEC code remains valid for the lifetime of the product.
As per recent amendments, you need to confirm/update your IEC details annually on the DGFT portal (even if there are no changes), between April and June. Failure to do so may deactivate the IEC.
Common Mistakes to Avoid
Incorrect PAN or mismatch in business name
Wrong bank details
Uploading unclear or incorrect documents
Missing annual IEC updates
Conclusion
IEC Registration is your business passport to the global market. Whether you're an individual exporter, MSME, or a large business house, IEC is essential to carry out international trade from India. The process is quick, cost-effective, and can be completed online with ease.
0 notes
Text
Exposing the Scam: Updated Fake Forex Brokers List You Must Avoid

The forex market offers enormous potential—but only when you’re working with trustworthy brokers. Unfortunately, many traders fall victim to fraud due to a lack of awareness. To avoid being scammed, staying informed with a fake forex brokers list is crucial for protecting your investments and peace of mind.
Understanding Fake Forex Brokers
Fake forex brokers are deceptive entities that pretend to offer legitimate trading services but operate purely to exploit unsuspecting traders. Instead of offering a genuine trading environment, they create the illusion of a functioning platform—complete with fake balances, manipulated charts, and fabricated profit margins.
These brokers often operate from offshore locations where regulatory oversight is minimal or nonexistent. They use aggressive sales tactics, pushing users to deposit more money quickly, promising quick profits, or offering exclusive "trading bonuses" that actually lock up your funds. Once money is deposited, communication becomes limited, withdrawal requests are stalled or denied, and customer support is either unresponsive or vanishes altogether.
In many cases, these brokers clone the websites and names of legitimate firms to appear more credible. They may even create fake regulator certificates or misuse license numbers from other companies to trick you into trusting them.
Before you invest, find out how fake brokers scam traders and how you can avoid becoming their next victim.
Explore now...
Brokers Known for Questionable Practices
Some brokers have raised serious red flags due to lack of licensing, offshore registrations, and poor withdrawal policies. Names that often come up in fraud reports include FX NextGen, Calibur Capital, Titan FX, FTE FX, Prime XBT, TradersWay, MidasGlobe, KronosInvest, Binomo, and CircleForex. These brokers have been associated with offshore operations or operate without recognized financial licenses, making them highly risky choices for any trader.

Red Flags to Watch For
✅ No regulation by trusted authorities like FCA, ASIC, or CySEC
✅ Unrealistic profit guarantees or “risk-free” trading claims
✅ Withdrawal delays or blocked fund access
✅ Aggressive marketing tactics like repeated deposit calls
✅ Fake testimonials or stolen online reviews
Protecting yourself from scams starts with vigilance. Always research broker backgrounds, read independent reviews, and confirm their licensing status with a regulatory body before investing.
FAQ: How to Stay Safe from Forex Scams
Q1: How can I verify a broker’s legitimacy? You should always check a broker’s license with financial authorities like the FCA (UK), NFA (US), or ASIC (Australia). These sites offer public records you can search by broker name.
Q2: What can I do if I’ve been scammed by a broker? Contact your bank to request a chargeback and file a complaint with financial regulators. You may also want to explore legal recovery services, though results can vary.
Q3: Are offshore brokers always risky? Not all offshore brokers are scams, but many operate without accountability. Always treat offshore-registered brokers with extra caution, and avoid those not licensed by reputable regulatory bodies.
Fake forex brokers are becoming more sophisticated each year. Traders must stay one step ahead by researching thoroughly and trusting only regulated, transparent platforms. Using a fake forex brokers list as a reference can help you steer clear of costly mistakes and ensure your trading journey is both secure and successful.
In short, staying informed about fake forex brokers could be your best defense against losing money to fraud. Never trade without verifying who you're dealing with.
0 notes
Text
Software Add-on nulled plugin 1.9.2

Unlock Premium Features with the Software Add-on Nulled Plugin If you're looking to supercharge your WooCommerce store, the Software Add-on nulled plugin is the perfect solution. This powerful plugin enables you to sell software products efficiently by offering license keys and seamless activation. With our free download of the nulled version, you can access all the premium functionalities without spending a dime—boosting productivity, sales, and user satisfaction instantly. What Is the Software Add-on Nulled Plugin? The Software Add-on nulled plugin is a premium WooCommerce extension designed to manage and distribute license keys automatically when selling digital software products. It's an indispensable tool for developers, digital product vendors, and online entrepreneurs. With its built-in automation, you no longer have to manually email activation keys—everything is handled swiftly and professionally. Technical Specifications Plugin Name: WooCommerce Software Add-on Version: Latest (Nulled) Compatibility: WooCommerce 4.0+ and WordPress 5.0+ License: GPL (Nulled for unrestricted use) Supported Products: Digital software, apps, eBooks, and license-based tools Key Features & Benefits The Software Add-on nulled plugin offers a wide array of features that streamline your software distribution: License Key Management: Generate, store, and distribute license keys with automated workflows. Secure Activation: Customers receive unique, encrypted license keys upon purchase. Expiration Control: Set license expiration dates for better subscription handling. Usage Limitations: Restrict license key usage based on your product licensing policy. Seamless Integration: Fully compatible with the latest WooCommerce versions and digital product types. Why Use the Software Add-on Nulled Plugin? Choosing the Software Add-on nulled plugin helps you bypass licensing restrictions while still enjoying the complete set of features. It’s ideal for small businesses or startups that want to scale their digital offerings without the overhead of recurring payments. The plugin delivers the same performance as the original premium version—minus the cost. Practical Use Cases Here are some of the top scenarios where the Software Add-on nulled plugin shines: Digital Agencies: Distribute custom-built software with ease. eBook Publishers: Offer DRM-protected eBooks with secure license keys. Software Startups: Handle beta access and license generation smoothly. Freelance Developers: Provide clients with licensed tools and updates. Installation Guide Download the Software Add-on nulled plugin from our website. Go to your WordPress dashboard → Plugins → Add New → Upload Plugin. Select the downloaded ZIP file and click "Install Now." Activate the plugin and configure your license key settings via WooCommerce settings. With just a few clicks, your digital storefront is ready to securely deliver software and keys to your customers without a hitch. FAQs Is the nulled version safe to use? Yes, the nulled version we provide is fully tested and clean. It does not contain any malicious code or security risks. Can I update the plugin? Since it's a nulled version, you won’t receive official updates. However, we periodically update the version on our website to keep you up to date. Is this plugin suitable for all types of digital products? Absolutely! Whether you're selling software, applications, eBooks, or anything else that requires licensing, this plugin is the right fit. Final Thoughts Streamline your software sales, automate license key distribution, and maximize customer satisfaction—all without breaking the bank. Download the Software Add-on today and unlock premium capabilities for free. This is your chance to take advantage of advanced features without paying a premium price. Looking for more powerful tools? Check out the FS Poster NULLED Plugin—another essential addition to your WordPress arsenal. For high-quality WordPress
themes, we also recommend Enfold NULLED for elegant, responsive design and outstanding functionality.
0 notes
Text
WhatsApp Data: The Engine Behind the World’s Most Popular Messaging App
Introduction
WhatsApp has become a cornerstone of digital communication, boasting over 2 billion active users globally. Whether it's a casual chat, a voice call, or a business inquiry, WhatsApp handles billions of interactions every day. Behind this seamless experience lies a massive amount of data—WhatsApp data—that powers the platform's functionality, user experience, security, and business capabilities.
From simple text messages to whatsapp data metadata and cloud backups, WhatsApp data encompasses a broad spectrum of digital footprints. In this article, we dive into what WhatsApp data includes, how it is used, what privacy concerns exist, and how individuals and organizations can leverage and protect it.
What is WhatsApp Data?
WhatsApp data refers to all forms of information generated, transmitted, stored, or processed through the WhatsApp platform. This includes:
1. User Data
Name, profile picture, status message
Phone number and contact list
Device type and IP address
Account settings (e.g., last seen, read receipts)
2. Message Content
Text messages
Voice messages
Images, videos, and documents
Stickers, GIFs, emojis
3. Call and Interaction Logs
Voice and video call history
Message timestamps
Message delivery and read receipts
4. Metadata
Information about messages (but not their content)
Who sent a message, to whom, at what time, from which device and IP address
Group memberships and group activity logs
5. Backup Data
Chats backed up to Google Drive (Android) or iCloud (iOS)
Media files included in backup, depending on user preferences
6. WhatsApp Business Data
Business profiles and catalogues
Automated messages (greetings, away messages, quick replies)
Customer interaction logs and analytics
How WhatsApp Uses Your Data
Although WhatsApp touts end-to-end encryption as a hallmark of its security model, the platform still uses and processes certain types of data for specific functions:
1. Message Delivery

Data ensures that messages are routed correctly from sender to receiver in a secure and timely manner.
2. Syncing Across Devices
With the multi-device feature, WhatsApp data is synced securely across multiple devices to ensure a consistent experience.
3. Spam and Abuse Detection
Metadata is analyzed to identify suspicious behavior such as bulk messaging, spam, or harassment.
4. Feature Enhancement
User interaction data helps WhatsApp improve features, fix bugs, and enhance performance.
5. Integration with Meta Ecosystem
While WhatsApp content remains encrypted, metadata (like device info and usage frequency) may be shared with Meta (its parent company) to personalize experiences on Facebook and Instagram, unless users opt out.
WhatsApp and Privacy: What’s at Stake?
Privacy has been at the heart of public debate around WhatsApp, especially after its 2021 privacy policy update. Here are the key privacy considerations related to WhatsApp data:
1. End-to-End Encryption
All messages, voice calls, and video calls on WhatsApp are end-to-end encrypted by default. This means only the sender and receiver can read or listen to the content—not even WhatsApp or Meta.
2. Metadata Collection
While message content is encrypted, metadata is not. This includes information about who you contacted, when, how often, and your location data inferred through IP addresses.
3. Data Sharing with Meta
In certain regions, WhatsApp shares user metadata with Meta for advertising and business intelligence. The specifics depend on the local legal framework and user consent.
4. Backup Security
Messages stored in cloud backups (Google Drive or iCloud) are not always encrypted unless the user enables encrypted backups. These backups can potentially be accessed by third parties, including law enforcement.
5. Group Privacy
While groups are secure, your phone number and profile picture are visible to all group members unless privacy settings are configured properly.
Downloading and Managing Your WhatsApp Data
WhatsApp allows users to download a report of their account information under the “Request Account Info” feature. This report includes:
Account creation date
Linked devices
Privacy settings
Profile information
Group memberships
However, it does not include message content or media files. For that, users must use chat export features or backups.
WhatsApp Business and Data Analytics
WhatsApp Business is designed for small to large businesses to engage with customers using automated, secure, and rich communication. The data collected here is incredibly valuable for customer service, marketing, and analytics.
1. Customer Data
Businesses collect names, contact details, and chat history, which help personalize support and product offerings.
2. Interaction Metrics
Metrics like response time, message delivery rates, read receipts, and customer engagement can be analyzed to improve performance.
3. APIs and CRM Integration
The WhatsApp Business API allows integration with CRMs and helpdesk software, enabling advanced data analysis and automation.
How Businesses Use WhatsApp Data
1. Customer Support
Brands like airlines, banks, and e-commerce platforms use WhatsApp to resolve customer queries, issue tickets, and provide real-time updates.
2. Transactional Messaging
Order confirmations, shipping updates, appointment reminders, and more are sent via WhatsApp using templates.
3. Marketing Campaigns
Although highly regulated, WhatsApp allows businesses to engage users with promotional content after explicit consent is provided.
4. Feedback and Surveys
Businesses use WhatsApp to gather customer feedback, often in the form of polls or NPS (Net Promoter Score) surveys.
Legal and Compliance Considerations
With great data comes great responsibility. WhatsApp data usage must comply with regional and international data protection laws.
GDPR (Europe)
Users must consent to data processing
Have the right to data access, correction, and deletion
Businesses must secure personal data and report breaches
CCPA (California)
Consumers have the right to know what data is collected and why
Businesses must disclose how WhatsApp data is shared or sold
DPDP (India)
Emphasizes data minimization, storage limitation, and user consent
WhatsApp faced scrutiny in India over its data-sharing policy with Meta
Security Risks Associated with WhatsApp Data
Despite its security architecture, WhatsApp data can still be at risk from:
1. Phishing and Malware
Scammers use WhatsApp to send fraudulent links that can steal data or install spyware.
2. SIM Swap Attacks
Hackers who gain control over a user’s SIM card can access WhatsApp accounts through OTP-based authentication.
3. Device Theft
If your phone is unlocked or your WhatsApp is not password-protected, anyone can access your messages and media.
4. Unencrypted Backups
If not encrypted, backups on cloud platforms can be a vulnerability point.
Best Practices to Protect WhatsApp Data
Enable Two-Step Verification Add an extra PIN code to prevent unauthorized access.
Use Encrypted Backups Turn on end-to-end encrypted backups in WhatsApp settings.
Be Cautious With Group Sharing Review group members before sharing sensitive information.
Manage Privacy Settings Control who sees your last seen, profile picture, about info, and status.
Avoid Clicking on Unknown Links Prevent phishing and potential malware by being cautious with messages from unknown contacts.
The Future of WhatsApp Data
As WhatsApp continues to expand its functionality—from payments in India and Brazil to desktop enhancements—its data ecosystem will grow even more complex.
1. AI and Chatbots
AI-driven chatbots will increasingly use WhatsApp data to offer personalized customer service and automate interactions.
2. Payments and Financial Data
With in-app payments, WhatsApp will handle sensitive financial data, requiring even stricter privacy protocols.
3. Enterprise-Grade Analytics
Large organizations will use business APIs and WhatsApp data analytics to streamline operations and customer journeys.
4. Greater Regulation
Expect tighter regulations and scrutiny over how WhatsApp and Meta handle user data, especially in the EU and Asia.
Thanks for reading..
SEO Expate Bangladesh Ltd.
0 notes
Text
Tackle Every Calculation Challenge with MegaCalculators.online
Tackle Every Calculation Challenge with MegaCalculators.online
Finding the right calculations handy and simple, can ease your mental burden in these fast paced technological times. For tailor-made personal, professional, and academic calculations, look no further than MegaCalculators.online. With a wide array of both personal and academic calculators organized in subcategories for easy navigation, satisfaction is guaranteed.
Whether you're a working individual managing grades, dealing with intuitively complex salary calculations, or merely monitor health and relationships, we've got your back.
Features Mega Calculators Online Provides
Because we all have different backgrounds and preferences, every user has unique needs regarding the specific tools required. To accommodate as many users as possible, at MegaCalculators.online we now feature an ever-growing collection of easy to use and powerful calculators. Some of the subcategories included are as follows:
Financial and Salary Calculators
Managing finances with friendly calculators has never been easier. Our useful tools already feature.
8th Pay Commission Salary Calculator- Get all the calculations done for you as per the 8th Pay Commission structure and receive your revised pay immediately.
Arbitrage Calculator- For trades dealing with price discrepancies between multiple markets, this is the ideal calculator.
Salary Hike Calculator- Figure out whether your appraisal gets you a raise or not.
Education & Academic Calculators
Simplifying a student’s life can be achieved with:
CGPA Calculator
Percentage to CGPA Converter Mark Percentage Calculator
Health & Wellness Calculators
Maintain your body and mind with:
**Ovulation Calculator – Helps plan conception activities in greater detail.
**Period Calculator– Helps out anticipate the subsequent cycle.
**Pregnancy Calculator – Accurately estimate the date when the baby is due to be born.
Professional & Work Tools
Excel at your workplace with:
Attendance Calculator – Effortlessly track your daily attendance.
Work Experience Calculator – Get accurate calculations of job tenure for resumes or formal purposes.
Cash Denomination Calculator – Makes handling and tallying cash an easy task.
Fun & Relationship Calculators
Make use of these fun tools as:
FLAMES Calculator** – Predicts relationships and rekindles nostalgic memories.
Business Name Numerology Calculator– Combine business identity with numerology.
Other Smart Tools**
Car EMI Calculator** – Determine the monthly payments required for a car loan.
LIC Surrender Value Calculator – Offers insight for the policy's surrender value.
Share Average Calculator – Designed for investors who want to calculate average share prices.
Terrabox downloader – Lets users easily download files stored on the Terrabox cloud platform.
Why Pick MegaCalculators.online
✅ Free & Easy to Us – No signup or download required. Everything is straightforward.
✅ Mobile Friendly – Our tools can be accessed on the go and even when not connected to the internet.
✅ Regular Updates – New calculators are added frequently to meet every niche.
✅ SEO Optimized & Fast Loading** – You will notice great and steady performance during your visits.
If you are looking for a platform to assist you in performing basic mathematics, keeping track of your finances or for anything fun, then MegaCalculators.online** will serve you right.
🔗 All our calculators can be accessed here** and let us help you do more with less effort daily.
1 note
·
View note
Text
Overview of Leading Banking Entities in ASX Bluechip Stocks
Highlights
Examination of major banking leaders within the ASX
Overview of market capitalisation and dividend distribution
Guidance on sourcing authoritative exchange information
The banking sector on the Australian Securities Exchange features some of the largest financial institutions by market capitalisation. The ASX Bluechip stocks in this segment include well-established bank entities that contribute substantially to daily trading volumes and overall index stability. Reputable names in this field have a history of delivering consistent dividend distributions and maintaining credit quality. Sector performance is influenced by factors such as central bank policies, regulatory developments, and macroeconomic indicators like lending activity and deposit flows. Evaluation of ASX Bluechip stocks performance can be supported by exchange data tools and company disclosures.
Leading ASX Bluechip stocks on the Index
Major constituents within this group include banks that have held positions within the top tier of the S&P/ASX Index. These institutions are characterized by large balance sheets and diversified revenue sources spanning retail banking, corporate lending, and wealth management divisions. Market capitalisation metrics often reflect the scale of operations across domestic and international markets. Trading activity in these names tends to account for a significant portion of total exchange turnover. Daily trading screens highlight liquidity trends among ASX Bluechip stocks in this sector.
Market Capitalisation and Trading Dynamics
Valuation measures for prominent banking names on the exchange are typically expressed in billions of local currency. The ASX Bluechip stocks in this listing command attention due to their share of total market value and high daily liquidity. Trading dynamics benefit from robust order books and tight bid-ask spreads, which facilitate efficient price discovery. Regulatory reporting frameworks require these entities to publish quarterly and annual results, providing transparent insights into net interest margins and non-interest revenue streams.
Dividend Distribution Profiles
Dividend payout ratios for leading banking names provide a perspective on cash returns to shareholders. The ASX Bluechip stocks in this category often operate under dividend policies that align with prudential guidelines, resulting in scheduled distributions twice per year. Historical payout trends can be reviewed through publicly available company announcements. The absence of speculative commentary ensures that readers can focus on peer-group comparisons and yield metrics without conjecture.
Monitoring Regulatory and Economic Indicators
Regulatory guidance and economic data releases have a direct bearing on the performance of ASX Bluechip stocks in the banking sector. Updates on official cash rate decisions, credit growth figures, and regulatory capital ratio requirements inform assessments of operational resilience. Market participants and research portals publish calendars of such events, enabling stakeholders to track key developments. This process supports a fact-based understanding of industry dynamics without relying on subjective forecasts.
Accessing Authoritative Information
Official exchange filings, regulatory disclosures, and company relations portals serve as primary sources for details on ASX Bluechip stocks. Dedicated segments on the exchange website provide real-time price data and corporate announcements. Third-party data aggregators offer comprehensive screening tools that filter by market capitalisation, sector classification, and dividend history. Users are encouraged to review the official documents directly to obtain verified performance metrics.
Sector Correlation Factors
Relationships between ASX Bluechip stocks and broader market indexes illustrate sector correlation dynamics. Price movements in this segment often align with shifts in interest rate expectations and global commodity trends. Historical data reviews show that changes in credit spreads and consumer confidence indices can coincide with price adjustments in these large-cap banking names. Trading platforms usually offer sector heat maps, enabling observers to visualize relative performance across multiple categories. Access to archival data supports research into correlation metrics over various time horizons. Correlation insights for ASX Bluechip stocks can inform benchmarking frameworks across different market cycles.
Call to Action
For ongoing updates on ASX Bluechip stocks, subscribe to the exchange’s notification service and consult official financial reporting releases to stay informed about the latest developments.
0 notes
Text
Master IT Infrastructure: Windows Server Administration Course in Australia
In today’s digitally driven world, servers are the foundation of every business’s IT operation. From hosting applications and managing user access to maintaining data security, servers do it all—and the professionals who manage them are critical to every organization's success. If you’re an IT professional in Australia looking to enhance your system administration skills, the Windows Server Administration Course in Australia offered by Xelware is your ideal next step.
This course is specially designed for both aspiring and experienced administrators, giving you practical, real-world skills to configure, manage, and maintain Windows Server environments effectively. Whether you're aiming to boost your resume, prepare for certification, or support your organization's infrastructure more confidently, this training is your gateway.
Why Learn Windows Server Administration?
Windows Server is one of the most widely used operating systems for managing enterprise-level IT infrastructure. It powers file servers, domain controllers, DNS, DHCP, and much more. With the continued growth of hybrid environments—mixing on-premise and cloud technologies—the need for skilled Windows Server administrators is only increasing.
By mastering Windows Server administration, you can:
Improve the performance, stability, and security of IT environments
Manage networks, users, and policies with precision
Ensure business continuity with proper backup and recovery practices
Reduce system downtime and boost productivity across the organization
Become a key resource in IT operations, infrastructure design, and support
What You’ll Learn in the Course
The Windows Server Administration Course in Australia from Xelware is based on Microsoft’s official curriculum and is updated to reflect the latest best practices and technologies in system administration.
Key areas covered include:
Installing and configuring Windows Server roles and features
Managing Active Directory Domain Services (AD DS)
Implementing DNS, DHCP, and IPAM
Maintaining server performance and monitoring systems
Ensuring security with group policies, file permissions, and firewall configurations
Automating tasks with PowerShell and administrative templates
Performing regular backups and disaster recovery
The course also emphasizes practical labs and case studies so you can apply what you’ve learned in realistic scenarios.
Why Choose Xelware in Australia?
Xelware is a trusted name in professional IT training, known for delivering industry-relevant content with expert instruction. Their Windows Server Administration Course is tailored for Australian learners and businesses, offering flexible schedules, local time zones, and trainers with hands-on experience in enterprise IT environments.
Here’s what sets Xelware apart:
Instructor-led sessions delivered live and online across Australia
Microsoft-certified trainers who teach from real-world experience
Interactive labs and assignments that build job-ready skills
Certification preparation and guidance to help you succeed
Post-training support and resources to reinforce your learning
Whether you're in Sydney, Brisbane, Adelaide, Melbourne, or working remotely from any corner of Australia, Xelware makes high-quality IT training accessible to you.
Who Should Take This Course?
This course is ideal for:
IT support professionals seeking to move into system administration
Network administrators wanting to broaden their expertise
System administrators responsible for Windows-based infrastructure
Students and recent graduates looking to specialize in server technology
IT managers who want to better understand their infrastructure
A basic understanding of networking concepts and the Windows operating system is recommended, but the course is structured to guide learners at all levels.
Final Thoughts: Build a Reliable IT Backbone
Every successful business relies on stable, secure, and efficient server infrastructure. As a Windows Server Administrator, you’ll play a vital role in ensuring the smooth operation of IT systems. The Windows Server Administration Course in Australia from Xelware gives you the skills and confidence to take on that responsibility with expertise.
0 notes
Text
Streamline Your Workflow: A Guide to Installing WalkMe for Teams

WalkMe for Teams offers a centralised hub that brings all your work applications into one easy-to-use interface. With this tool, your organisation can provide employees with tailored access to important resources and improve overall productivity. This guide explains the steps required to install WalkMe for Teams, ensuring a smooth deployment by your IT department.
Preparing for Installation
Before beginning the installation, ensure that your IT department is ready to manage the process. WalkMe for Teams is designed to be deployed via the Teams admin centre rather than by individual users. This centralised approach means your organisation maintains control over app distribution and customisation. Begin by accessing the Microsoft Teams admin centre at https://admin.teams.microsoft.com/policies/app-setup.
Setting Up the App Policy
The first step is to create an app setup policy:
Sign in to the Teams admin centre: Once logged in, navigate to Teams apps > Setup policies.
Add a new policy: Click on Add and provide a clear name and description for the policy.
Include WalkMe in Installed Apps: Under the Installed apps section, select Add apps. In the search pane, type “WalkMe” and then click Add to include it in the policy.
Pin the App for Better Engagement: Scroll down to the Pinned apps section, click Add apps, search for “WalkMe”, and then click Add. For optimal user engagement, reposition the WalkMe app higher on the pinned apps list.
Assigning the Policy to Users
After configuring the app policy, the next step is to decide which user groups will receive the WalkMe app:
Return to the policies page: Go back to https://admin.teams.microsoft.com/policies/app-setup.
Group Policy Assignment: Select Group policy assignment > Add. Choose the appropriate Azure AD group. For organisations covering all employees, select a group that represents the entire company.
Apply the Policy: After selecting the group, choose the newly created policy from the list and click Apply.
Creating an Azure AD Group
To ensure that all relevant users are included:
Log in to Azure AD: Visit https://portal.azure.com/ and click on Groups.
Create a New Group: Choose New Group, set the group type to Security, and provide a name and description.
Set Membership to Dynamic User: Select Dynamic user as the membership type and add a dynamic query. For example, use the condition where “userPrincipalName” Contains “@YOUR_DOMAIN.COM”. Replace YOUR_DOMAIN with your actual domain name.
Save and Wait: After saving the query, the group will populate with all users matching the criteria.
Customisation and Branding
WalkMe for Teams is adaptable to your organisation's branding:
Short Name and Full Name: Update these in the manifest file to display the appropriate names for your tab.
Icons: Replace the default icon files with your custom PNG files. Ensure that the icon dimensions meet Microsoft’s guidelines.
Additional Resources and Support
For further guidance on customisations and best practices, check out the experiences shared by our WalkMe partner Australia. If you need assistance with other Teams configurations, refer to resources available at WalkMe microsoft teams. Reading through WalkMe customer stories can provide real-world examples of successful deployments and benefits realised by other organisations.
Final Thoughts
By following this guide, your IT department can install WalkMe for Teams with confidence. This process creates a centralised hub that simplifies access to applications and resources, supporting digital adoption and boosting overall productivity. Enjoy a smoother, more streamlined work experience with WalkMe for Teams.
The author is a digital adoption expert with deep insights into enterprise systems, user engagement, and practical deployment strategies. Their expertise spans platform comparisons, installation guides, and best practices for tools like WalkMe, Salesforce, and ERP solutions. For expert digital adoption solutions, visit: https://www.guidemesolutions.com/
0 notes
Text
On-Demand Letter Printing and Mailing – Send Custom Letters Anytime
Gone are the days when sending a personalized letter meant finding a printer, buying envelopes, and heading to the post office. On-demand letter printing and mailing services have revolutionized how individuals and businesses communicate. Whether it's a thank-you letter, a formal notice, or a promotional message, these services let you send custom letters whenever you need to.

What Is On-Demand Letter Printing and Mailing?
On-demand letter printing and mailing is a cloud-based service that lets users create, customize, and send letters instantly. Once your letter is uploaded or composed, it is professionally printed, enveloped, and mailed by the service provider.
Advantages of On-Demand Mailing
24/7 Accessibility: Send letters anytime, from anywhere.
Fully Customizable: Add logos, headers, branding elements, or personalized messages.
Scalable for Any Volume: Send one letter or thousands without any manual work.
High-Quality Print: Commercial-grade printing ensures professional results.
No Inventory Needed: No need to store stationery or postage.
Environmentally Friendly: Some services use eco-friendly paper and carbon-neutral delivery options.
How to Send a Letter On-Demand
Compose or Upload: Write your letter or upload an existing file.
Personalize: Add custom details like the recipient’s name, merge fields, or branding.
Choose Delivery Preferences: Select printing options, color or B&W, and delivery speed.
Review and Pay: Finalize the document and process payment.
Printing & Mailing: The provider handles everything from printing to posting.
Popular Use Cases
Real Estate: Send letters to potential clients or neighborhood farming letters.
Finance: Deliver compliance letters, billing notices, or financial summaries.
Nonprofits: Send donation appeals, event invites, or thank-you letters.
E-commerce: Provide custom order updates, return information, or discount offers.
HR Departments: Mail employment letters, policies, or onboarding documents.
What Makes a Great On-Demand Mailing Platform?
Intuitive user dashboard
Variable data printing for personalization
Quick turnaround time
Affordable pricing and bulk discounts
Document storage and templates
Mail tracking and reporting
Conclusion
On-demand letter printing and mailing gives you the flexibility to send personalized communications whenever the need arises. Whether you're running a campaign or sending a one-off letter, this solution saves time, reduces hassle, and guarantees professional delivery. It’s time to upgrade your communication strategy with the power of on-demand mailing.
youtube
SITES WE SUPPORT
Print Documents Online – Wix
0 notes
Text
Import Export Code (IEC) Registration: Eligibility & Requirements

Businesses now need to adhere to international trade regulations because of India's growing worldwide trade. Getting the IEC Code is the first step for every business, whether it is an established company venturing into the import-export industry or an entrepreneur seeking to investigate new international markets. The Directorate General of Foreign Trade (DGFT) issues the Import Export Code, which serves as a special identifying number for companies conducting cross-border trading. A legal and essential prerequisite for any Indian company that imports or exports goods or services is IEC Code Registration. The IEC Registration procedure, eligibility requirements, necessary paperwork, and how frequent IEC updates guarantee smooth international trade compliance are all covered in this extensive handbook.
What is an IEC Code?
The Import Export Code (IEC) is a 10-digit alphanumeric code issued by the DGFT under the Ministry of Commerce and Industry, Government of India. It is mandatory for every individual or business engaged in the import or export of goods and services from India.
Without valid Import Export Code Registration, businesses cannot:
Clear shipments through customs
Receive foreign currency payments
Avail export subsidies or benefits under foreign trade policies
Hence, IEC Code Registration not only confirms compliance but also increases a business’s credibility in global markets.
Why is IEC Code Important?
IEC acts as the passport for international trade. Here's why it is essential:
Customs Clearance: IEC is mandatory for clearing shipments at Indian ports and airports.
Banking Compliance: Banks require IEC to authorize foreign remittances for import/export transactions.
Trade Benefits: Entities with IEC can avail benefits under various government schemes like RoDTEP, MEIS, and SEIS.
Global Expansion: It facilitates expansion to international markets and builds trust with foreign buyers or sellers.
Without IEC Registration, even the most promising international deals can hit a regulatory roadblock.
Who Needs IEC Code Registration?
IEC Registration is required by:
Businesses involved in the import of goods or services
Exporters of physical goods or digital services
Proprietors, partnerships, LLPs, companies, trusts, or HUFs engaged in cross-border trade
E-commerce sellers shipping internationally
Note: Even if you are a freelancer providing services abroad and receiving foreign currency payments, you must obtain an IEC.
Who Is Exempted from IEC Registration?
While most businesses involved in import/export activities must have an IEC, the following are exempted:
Departments and ministries of the Central or State Government
Individuals importing or exporting goods for personal use unrelated to trade or manufacturing
Import/export activities covered under special categories like the diplomatic corps or defense-related imports
For all others, especially businesses, Import Export Code Registration is non-negotiable.
IEC Code Registration Eligibility Criteria
There are no complex eligibility conditions, making IEC Registration simple and accessible. However, applicants must make certain:
Valid PAN: The applicant (individual or entity) must have a valid Permanent Account Number (PAN).
Business Registration: If applying as an organization, it must be legally registered under applicable Indian laws.
Bank Account: A current bank account in the entity’s name (matching PAN) is required.
Operational Premises: The business must have a valid address with supporting proof.
Digital Signature (DSC): For companies and LLPs, DSC is mandatory for online filing.
There is no minimum turnover requirement, and even startups or freelancers can apply for an Import Export Code.
How to Apply for Import Export Code Registration: Step-by-Step Process
The Import Export Code Registration process is completely online and user-friendly. Follow these steps:
Step 1: Visit the DGFT Portal
Go to the website .
Create a new user account if not already registered
Step 2: Choose IEC Application
Login to your account
Go to the ‘Services’ section and select ‘Apply for IEC’
Step 3: Fill in Business Details
Provide accurate details about your business, including:
Name of applicant/entity
PAN and address
Bank details
Type of business (proprietor, firm, company, etc.)
Step 4: Upload Required Documents
Confirm that all supporting documents (PAN, address proof, canceled cheque, etc.) are scanned and ready for upload in the prescribed format.
Step 5: Payment of IEC Registration Fee
Pay the application fee (INR 500 as of the latest notification) online via net banking or UPI.
Generate payment acknowledgment.
Step 6: Submit the Application
Once everything is verified, submit the application.
Upon approval, you will receive the IEC Code digitally, usually within 1-2 working days.
Recognizing IEC Update Requirements
Once you receive your IEC, it is valid for a lifetime and does not require renewal. However, as per recent changes introduced by DGFT:
Annual IEC Update Is Mandatory
From 2021 onward, all IEC holders must update their IEC information annually—even if no changes have occurred.
Key Points:
The IEC update must be done between April and June each year.
Failure to update will result in deactivation of the IEC.
Reactivation can be done later by submitting the update form.
This mandatory IEC update confirms that DGFT has up-to-date and accurate information for all entities involved in import/export.
Common Mistakes to Avoid During IEC Code Registration
Here are some frequent errors to watch out for:
Entering incorrect PAN or business details
Uploading documents in the wrong format or file size
Using a bank account not in the name of the entity
Missing the IEC update deadline after issuance
These mistakes can delay the approval or lead to rejection. Confirm complete and accurate information before submitting.
IEC Code for Service Exporters
Many people believe that IEC Code Registration is only for physical goods. However, that is not true. Service providers, freelancers, software developers, digital marketers, and consultants who receive foreign currency payments for services are also required to have an IEC Code. This enables them to receive foreign remittances legally and participate in global freelancing and service marketplaces.
Assumption
In India, the IEC Code is an essential component of every import-export enterprise. Timely IEC Code Registration guarantees compliance, eligibility for government advantages, and continuous cross-border trade, regardless of the size of your business. The procedure is simple, requires little paperwork, and may be finished online. Don't forget to update your IEC every year; doing so confirms smooth operations and keeps your company in compliance with changing requirements. Getting and keeping a valid Import Export Code opens the door to international business expansion in addition to fulfilling legal obligations.
FAQs on IEC Registration
Q1. Is GST mandatory for IEC Code Registration? Ans No. While GST can be added to the IEC profile, it is not mandatory for the IEC application.
Q2. Can one IEC be used for multiple branches or locations? Ans Yes. One IEC can be used across all branches of the same entity. However, address details must be added in the profile.
Q3. What is the validity of the IEC Code? Ans IEC is valid for life. Only an annual IEC update is required every year between April and June.
Q4. Is there any penalty for not updating IEC? Ans Non-updated IECs are deactivated and cannot be used until reactivated. No monetary penalty is levied but it may delay trade.
0 notes
Text
Returns and Warranty Requests nulled plugin 2.6.4

Unlock Seamless Warranty Management with Returns and Warranty Requests Nulled Plugin If you're running a WooCommerce store and looking for an all-in-one solution to handle product warranties and return requests, the Returns and Warranty Requests nulled plugin is exactly what you need. This powerful tool empowers store owners to efficiently manage post-purchase services without the need for expensive subscriptions. Get this premium plugin for free from our platform and streamline your customer support like never before. Why Choose the Returns and Warranty Requests Nulled Plugin? The Returns and Warranty Requests nulled plugin offers seamless integration with your WooCommerce store, helping you automate and manage all customer return and warranty requests in a centralized dashboard. Whether you're dealing with defective items, refund claims, or general product issues, this plugin ensures a transparent and reliable process for both store owners and customers. Technical Specifications Plugin Name: Returns and Warranty Requests Compatible With: WooCommerce 4.x and higher License Type: GPL (Nulled Version) PHP Version: 7.4 and above Multisite Support: Yes Language Support: English (default), WPML compatible Features and Benefits Automated Return Process: Streamlines return, refund, and warranty requests directly from the user's account page. Custom Warranty Terms: Assign different warranty durations to individual products or categories. Email Notifications: Keep your customers informed with automated updates on their request status. Advanced Admin Panel: Easily monitor and manage all active and past warranty claims from a single dashboard. Documentation & User Guidance: Built-in tips and hints to help you configure the plugin with ease. Use Cases The Returns and Warranty Requests is ideal for eCommerce websites that sell electronics, fashion, appliances, or any product that benefits from warranty coverage. With this plugin, you can: Handle defective or damaged product returns efficiently Provide extended warranties to enhance customer trust Allow customers to upload images and details to support their claim Reduce manual communication and errors in return processing How to Install the Returns and Warranty Requests Nulled Plugin Download the plugin ZIP file from our website. Log into your WordPress dashboard and navigate to Plugins > Add New. Click Upload Plugin and select the ZIP file. Install and activate the plugin. Navigate to WooCommerce > Settings > Warranty to customize your return policies and warranty rules. Once installed, your store will instantly support hassle-free return and warranty processing—enhancing customer satisfaction and loyalty. Frequently Asked Questions (FAQs) Is it safe to use the Returns and Warranty Requests nulled plugin? Yes, the version available on our website is thoroughly tested and safe for use. We ensure all nulled plugins are clean, malware-free, and ready for secure installation. Can I use this plugin with my existing theme? Absolutely! The Returns and Warranty Requests nulled plugin is designed to be fully compatible with all modern WooCommerce themes and builders. Will this plugin affect my website speed? No. The plugin is optimized for performance and has minimal impact on website load time when configured properly. Where can I find other nulled plugins like this? If you're interested in enhancing your site's security, check out our iThemes Security Pro NULLED plugin available for free. Is there an SEO plugin available too? Yes! You can download Yoast seo nulled to boost your search engine visibility effectively. Final Thoughts The Returns and Warranty Requests is the go-to solution for WooCommerce store owners looking to streamline post-purchase support while avoiding recurring costs. By downloading this plugin for free, you're not just saving money—you’re elevating your customer service and building long-term trust with your buyers. Don’t miss
out on the opportunity to enhance your store’s credibility and functionality—download now and take control of your warranty management system effortlessly.
0 notes
Text
Achieving a Greener Lifestyle: The Sustainability Impact of Remote Work
Working with a partner or single-handedly can be a boring task. Moreover, we can depend on our resources if we do remote work. In addition, one can have the comfort of not traveling or doing the task in the presence of a senior. Although it needs to get updates at times, it is a way for us to develop our present and do work for the future.
The Relation with Sustainability
We develop new solutions for the better interface of the users. One of these solutions is Cloud Computing. A better insight into this topic can be the role of the cloud in providing remote jobs for example. Hence, to sustain these newer forms of growth we use Remote Work.

Remote Working benefits instead of using software to produce large chunks of data building up piles of unused files.
Newer software has a chance to compete in a market full of policies.
Businesses can expand without the need for third-party companies.
Our business offers an array of web-based solutions as per your needs.
Introduction of International Business Relations
Now, the usage of external servers to keep the data centers running smoothly can be dealt with formally. Brands have the chance to build their value online in a great manner. Hence, we as a company can grow your career and offer APIs for remotely working on a project that you wish. Thus, we offer our help by the name of ZenithCloud.

Conclusion
If you want to form good relations and take a step further in a world of great scopes, please contact us at [email protected]. Our sales team and AI chat expert can help you in many ways.
1 note
·
View note